In the ever-evolving landscape of technology, security, and system optimization, tools and software solutions play a vital role in maintaining the health of modern systems. One of the common concerns among users is compatibility and support for specific applications or systems. A recent development in this space involves the incompatibility of Bypassio with Gzfit’s Advance System Care. This incompatibility has sparked discussions and queries among users and experts alike. This article delves into the reasons behind this limitation, its implications, and how Gzfit Advance System Care ensures a secure and optimized environment.
Understanding Gzfit Advance System Care
Gzfit Advance System Care is a state-of-the-art software designed to enhance system performance while providing robust security measures. Its core functionalities revolve around the optimization of system resources, elimination of malware, protection against potential threats, and maintaining data integrity.
The system employs advanced algorithms that proactively monitor system activities and detect any anomalies. By leveraging machine learning, Gzfit Advance System Care adapts to evolving threats, ensuring that the system is always protected. This capability, however, also makes it selective about the applications it supports, such as Bypassio.
What is Bypassio?
Bypassio is a tool often associated with bypassing certain restrictions or security protocols on devices. While its applications are diverse, they frequently include accessing restricted system features, removing specific software limitations, or unlocking functionality that is otherwise unavailable.
Despite its utility in certain cases, Bypassio raises significant security concerns. These concerns primarily revolve around the potential exploitation of vulnerabilities, unauthorized access to systems, and compatibility issues with advanced security tools like Gzfit Advance System Care.
The Incompatibility Explained
The primary reason Gzfit Advance System Care does not support Bypassio lies like its functionalities. The core objective of Gzfit is to secure and optimize systems, ensuring no unauthorized or potentially harmful applications operate within its environment. On the other hand, Bypassio’s purpose often contradicts these principles.
Key Factors for Incompatibility:
- Conflict with Security Protocols:
Gzfit employs stringent security protocols to safeguard systems against malware and hacking attempts. Bypassio’s bypassing mechanisms often trigger these protocols, marking it as a potential threat. - Violation of Data Integrity:
One of the pillars of Gzfit Advance System Care is maintaining data integrity. Any tool that manipulates or overrides standard operating procedures, as Bypassio does, is automatically flagged as incompatible. - Resource Optimization Concerns:
Gzfit is designed to optimize resources, ensuring a seamless user experience. Tools like Bypassio, which can alter system-level operations, disrupt this optimization process, leading to inefficiencies. - Risk of Unauthorized Access:
By allowing unauthorized access or bypassing security features, Bypassio creates potential vulnerabilities. Gzfit Advance System Care identifies and prevents such risks, resulting in the non-support of Bypassio.
The Role of Advanced Algorithms in Gzfit
At the heart of Gzfit’s robust functionality are advanced algorithms that continuously monitor and adapt to system activities. These algorithms play a crucial role in identifying applications like Bypassio and ensuring they are not permitted to run.
The following table highlights some of the critical algorithmic functions and their impact on system security and optimization:
| Algorithmic Function | Impact on System |
|---|---|
| Threat Detection | Identifies and eliminates potential threats, including unauthorized applications like Bypassio. |
| Behavioral Analysis | Monitors application behavior to detect anomalies and flag suspicious activities. |
| Resource Allocation Optimization | Ensures system resources are used efficiently, preventing unnecessary consumption by incompatible tools. |
| Real-Time Updates | Adapts to emerging threats and software to maintain compatibility and security. |
| Data Protection Protocols | Secures sensitive information against unauthorized access or manipulation. |
Implications for Users
The incompatibility between Bypassio and Gzfit Advance System Care might initially seem restrictive, but it reflects Gzfit’s commitment to ensuring user safety and system efficiency.
Benefits of Gzfit’s Approach:
- Enhanced Security: Users benefit from a system that prioritizes security, ensuring protection against external and internal threats.
- Seamless Performance: By optimizing resources and preventing unauthorized tools from running, Gzfit maintains smooth system operation.
- Long-Term Reliability: The elimination of potentially harmful applications extends the life of the system and reduces maintenance costs.
On the flip side, users relying on Bypassio for specific purposes might need to seek alternative tools or adjust their practices to align with Gzfit’s protocols.
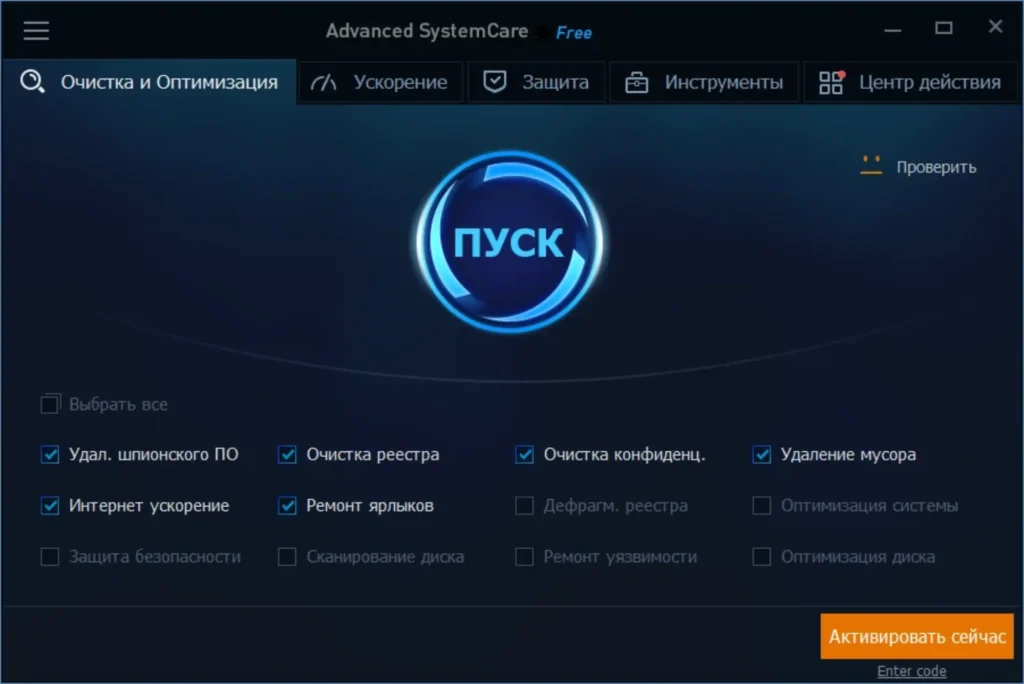
Alternatives and Workarounds
For users requiring similar functionality to Bypassio, exploring authorized and compatible alternatives is essential. Many tools in the market offer legitimate ways to achieve system customization or enhanced access without compromising security.
Additionally, engaging with Gzfit’s customer support team might provide insights into resolving specific compatibility concerns or identifying configurations that align with their system care protocols.
The non-support of Bypassio by Gzfit Advance System Care underscores the importance of balancing system functionality with security and efficiency. While Bypassio offers certain conveniences, its potential risks make it incompatible with a tool like Gzfit, which prioritizes safeguarding systems against all vulnerabilities.
Users are encouraged to embrace the advanced features of Gzfit Advance System Care and explore secure alternatives to achieve their objectives. By aligning with tools designed for optimization and security, users can enjoy a seamless and worry-free digital experience.